
Are you hesitant to use a home monitoring video camera because you’re afraid of hackers?
It’s an understandable concern: If your wireless router, network, IP camera, computers and smart phone aren’t all properly secured, prying eyes can view your video stream and even pinpoint your geographic location. The website insecam.org claims to be the world’s biggest directory of online surveillance security cameras. Hundreds of live video streams from IP cameras all over the world can be viewed through this website.
The most important precautions you can take are to create hack-proof passwords and to keep them securely stored. In fact, Insecam’s website states that if you don’t want your IP video camera to show up on their website, “The only thing you need to do is to set the password of your camera.” When asked if the IP cameras accessible through Insecam’s website have been hacked, their response is: These cameras are not hacked. All cameras listed on the site do not have any password protection. That’s just it—many people routinely skip replacing default passwords with their own.
Starting with passwords, here are the top five steps you can take to use your IP camera safely:
1. P A S S W O R D S
Create strong passwords and store them securely. If you neglect to create your own password, there are many ways hackers can easily find your device’s default password. For example, there are websites such as routerpasswords.com that list every router manufacturer’s default passwords.
It’s imperative you create secure passwords for your:
- Camera
- Wireless Router (How to Change Your Wireless Router’s Password)
- Wireless Network (How to Change Your Wireless Network’s Password)
- Devices used for viewing your IP camera such as your smart phone, laptop, PC, tablet, etc.
Components of a secure password:
- Use numbers, upper and lower case, as well as symbols
- Make the password a minimum of ten characters. The longer your password, the more difficult it is to crack.
- Choose a sequence of characters that aren’t predictable – don’t use “1234”, your birth date or your pet’s name all by itself
Example of how to create a secure password:
If your pet rats are named Twyla and Henderson, create a password with abbreviations of their names combined with numbers and symbols: Hend4Twy=sTarS*
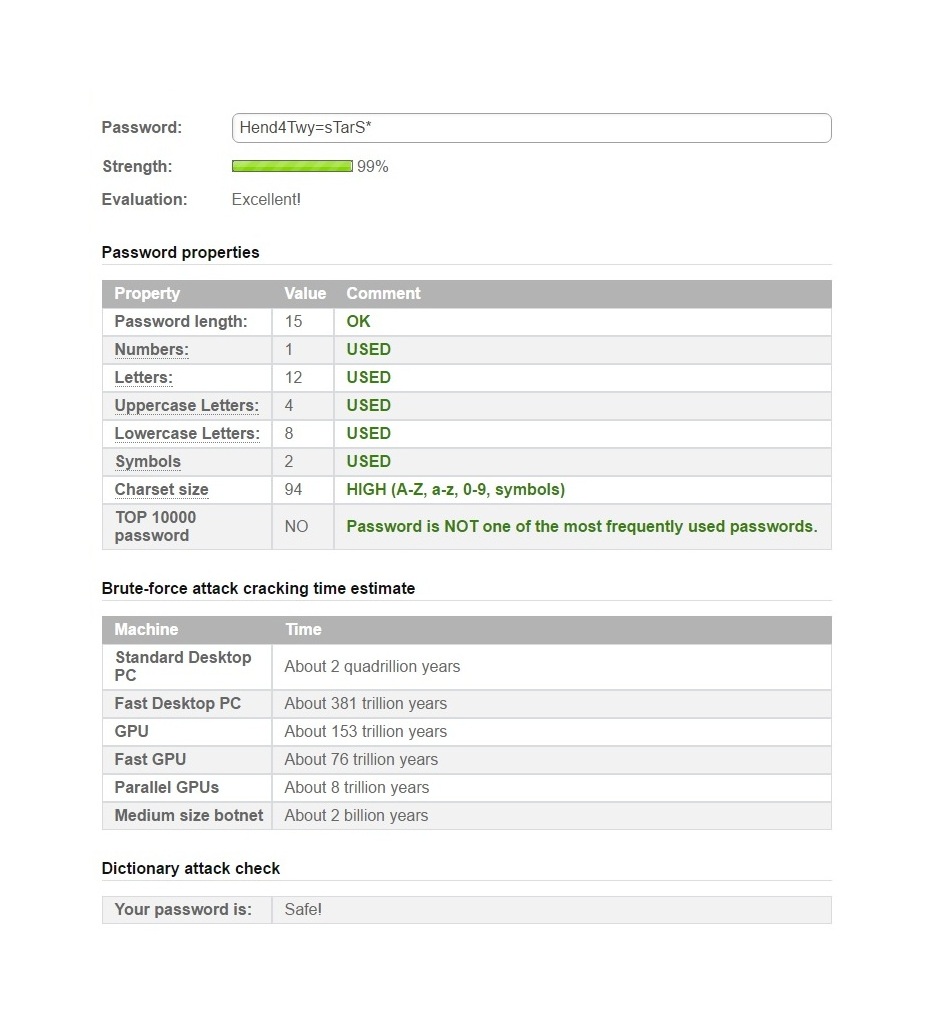
Check to see how your password ranks by using a password checker such as the one found on Online Domain Tools. The password Hend4Twy=sTarS* checks out as having a password strength of 99% and is evaluated as being Excellent. In addition, the brute force attack cracking time estimate by a medium size botnet is about 2 billion years. I’d say that’s pretty safe.
Here’s the Online Domain Tools password checker report for the password, Hend4Twy=sTarS*:
Secure your passwords:
- Don’t share your passwords on a phone, by texts or email. Any company that requests your passwords is out to scam you.
- Use different passwords throughout your accounts. Otherwise, if your password was stolen, all of your accounts with that password could be compromised.
- Keep your passwords in a secure, discreet location. You can even use a password management tool. One such service, LastPass, offers a free (as well as a paid) service for securely storing your passwords.
- Change your passwords regularly. Keep in mind passwords are usually stolen without your knowledge and stolen password(s) aren’t always used immediately. Place a reminder in your smart phone or an online calendar to help you remember to change your passwords every three to six months.
2. S E C U R E Y O U R W I R E L E S S N E T W O R K
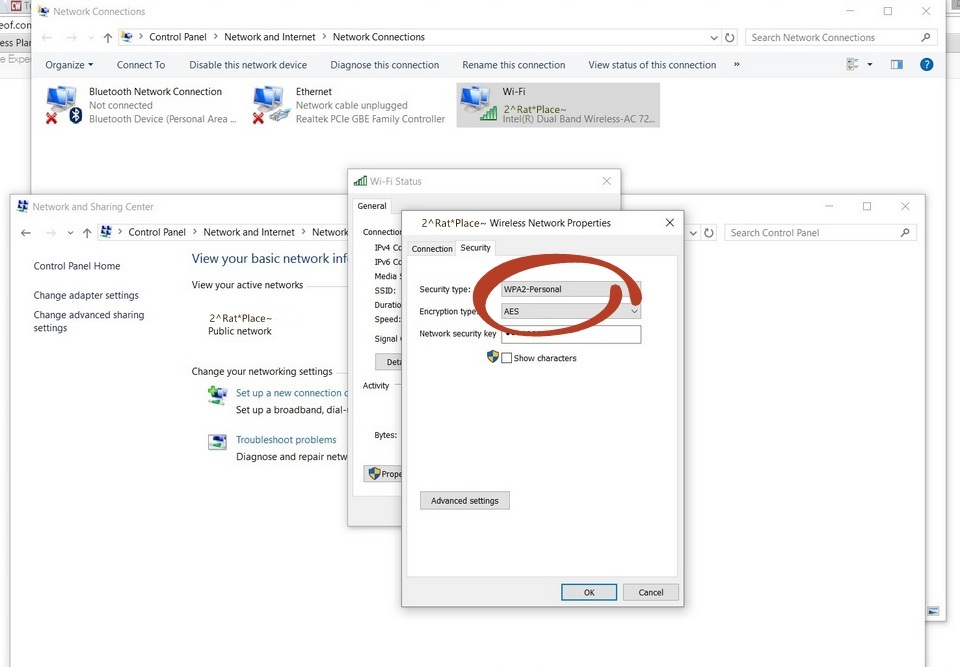
WPA2-AES is the current highest level of wi-fi security. WPA stands for Wireless Protection Access and has been updated, which is why it’s now called WPA2. AES (Advanced Encryption Standard) consists of an encryption algorithm that’s used worldwide (including by government) to protect data from getting into the wrong hands. Until an even better means of protection is developed, make sure WPA2-AES is selected as your wireless network’s encryption method.
Here’s where to check to make sure your wireless is set to WPA2-AES. The following screenshot shows the Wireless Network Properties in Windows 10 and will, of course, be displayed differently depending upon your device’s operating system:
Just in case you’re curious—as well as to ease any apprehensions—here’s how to find out if others are using your wireless network.
3. B U Y A S E C U R I T Y – M I N D E D I P C A M E R A
If you’re at all concerned about your video stream being viewable by others, make sure to purchase an IP camera with encryption protection.
After having won a Vimtag video surveillance camera, I’ve fallen in love with this brand. The Vimtag camera I won (the VT-361) has financial level encryption protection (using RSA/DH/DES, MD5, SHA/CRC/BASE64 encryption algorithms).
4. A C C E S S Y O U R C A M E R A S A F E L Y
Access your camera from a secured url. The address to the log-in page should begin with https. If you log into a page whose address is unsecured, (Ex: “http”—without an “s” at the end,) your connection is not encrypted and is consequently vulnerable to being accessed by others who can view your video feed.
Your PC, smart phone and any other devices used to view your IP camera’s video stream should be set up with a lock screen password. Any apps used to access your IP camera should also be accessible only after entering your personally selected user name and password.
5. U P D A T E R E G U L A R L Y
Update your devices as well as all software and apps you use as soon as updates are available.
Don’t let the fea r of being hacked stop you from using an IP video camera to monitor your pet rats
r of being hacked stop you from using an IP video camera to monitor your pet rats
The benefits are many—from being able to observe a sick rat, check in on newly introduced rats to simply finding out when your pet rats are ready to play.
By using the tips outlined here, you can greatly reduce any chances of security breaches, allowing you to enjoy using your IP camera with confidence.
NOTE: Vimtag has new cameras now available: The Vimtag P1 and the Vimtag M1. A review of the Vimtag P1 is coming soon!
 r of being hacked stop you from
r of being hacked stop you from 






Leave a Reply